Role in the pipeline
Størm Engine is the system-level enforcement pipeline that admits PQC-bound events, normalizes semantics, runs inference, updates behavioural and graph state, and emits bounded decisions within configured latency tiers.
A deterministic pipeline with bounded AI.
Størm Engine treats every event as a state transition.
Deterministic preprocessing feeds probabilistic inference.
Policy-first fusion bounds actions and seals evidence.
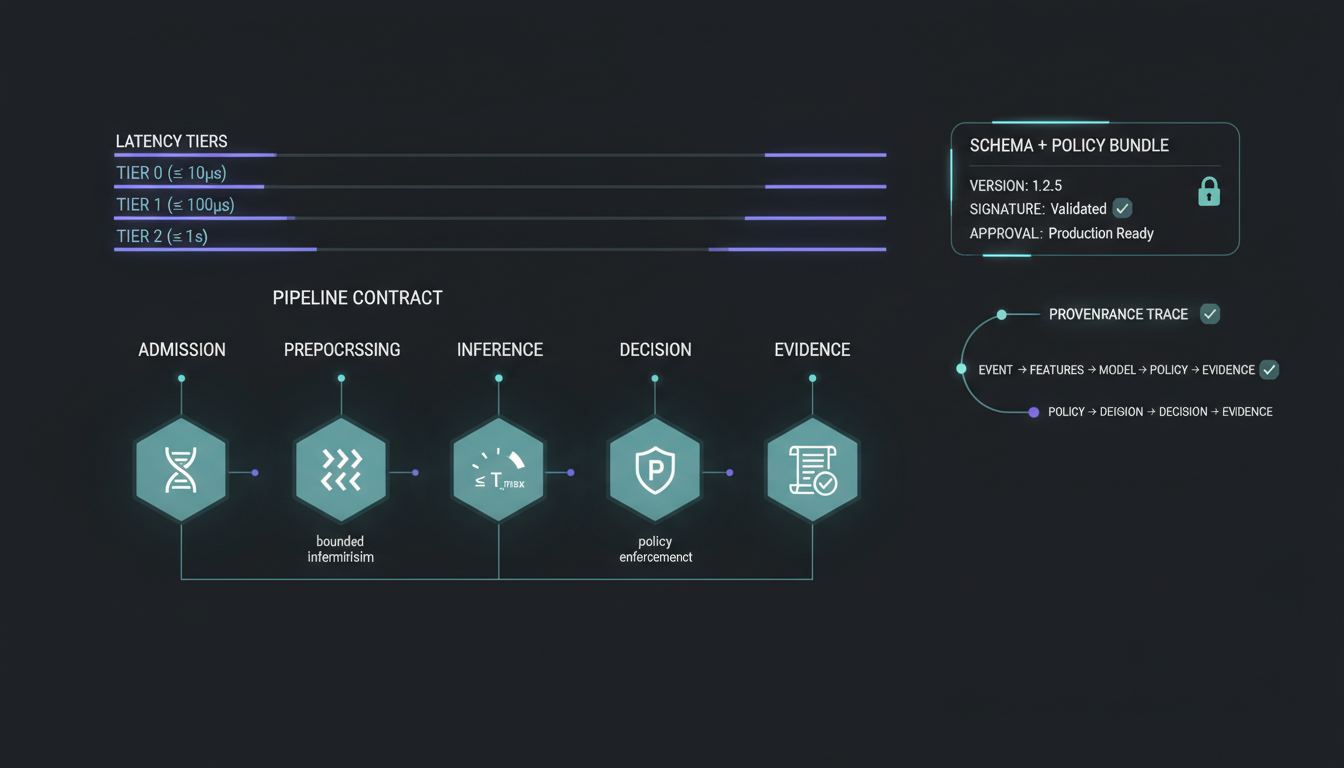
Pipeline contracts.
- Admission requires PQC session binding, ordering, and schema validation.
- Deterministic preprocessing yields stable feature vectors.
- Probabilistic inference is bounded by policy constraints.
- Latency targets are tiered and configurable per stream.
- Decision objects and provenance are sealed in StørmVault.
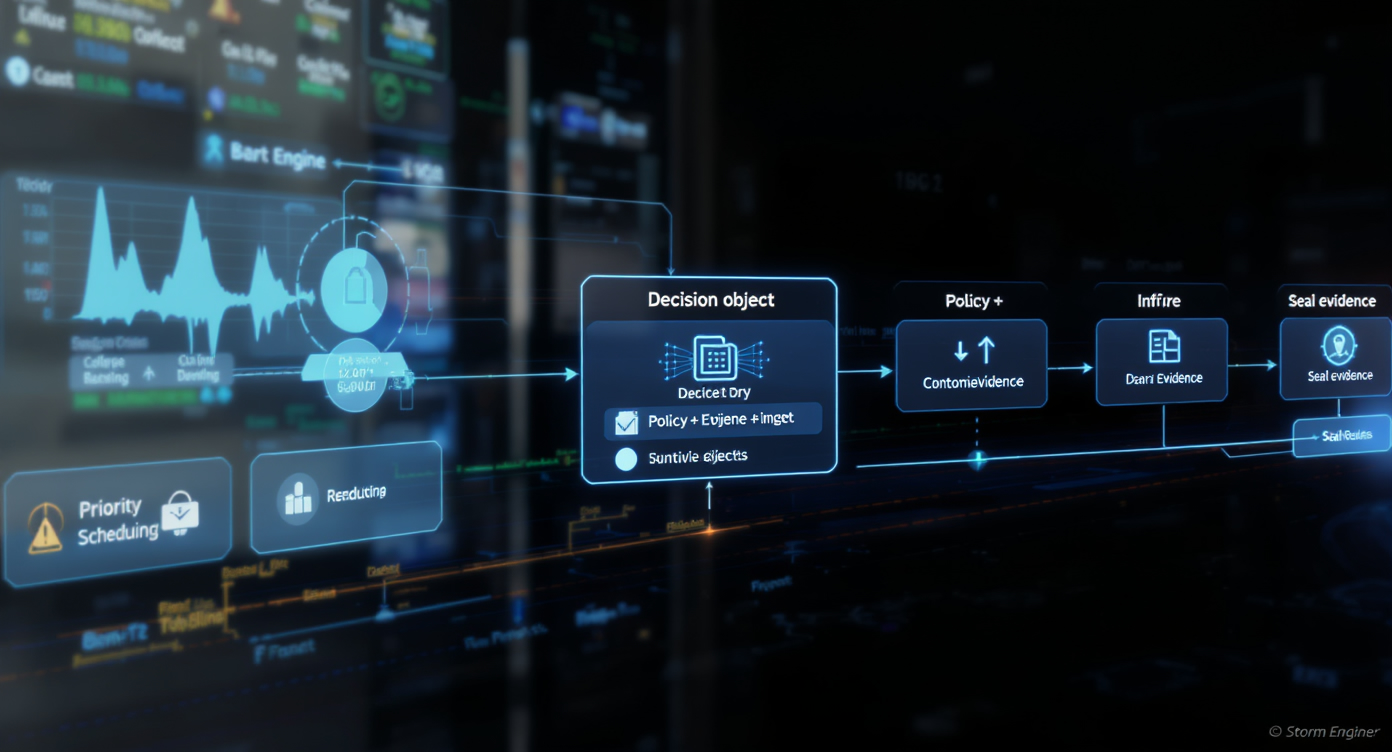
Product map
Pipeline sequence from admission to evidence.
StørmTrust
Session binding and artifact integrity.
StørmPrep
Canonical events and deterministic features.
StørmAI
Event-time inference signals.
StørmBehaviour
Behavioural state and invariants.
StørmGraph
Reachability and blast radius.
StørmDecision
Policy-first decision objects.
StørmControl
Enforcement execution with receipts.
StørmVault
Sealed chain-of-custody evidence.
System contracts
- Bounded latency targets per enforcement tier.
- Deterministic preprocessing and replay safety.
- Provenance for models, policies, and schemas.
- Evidence sealing and chain-of-custody.

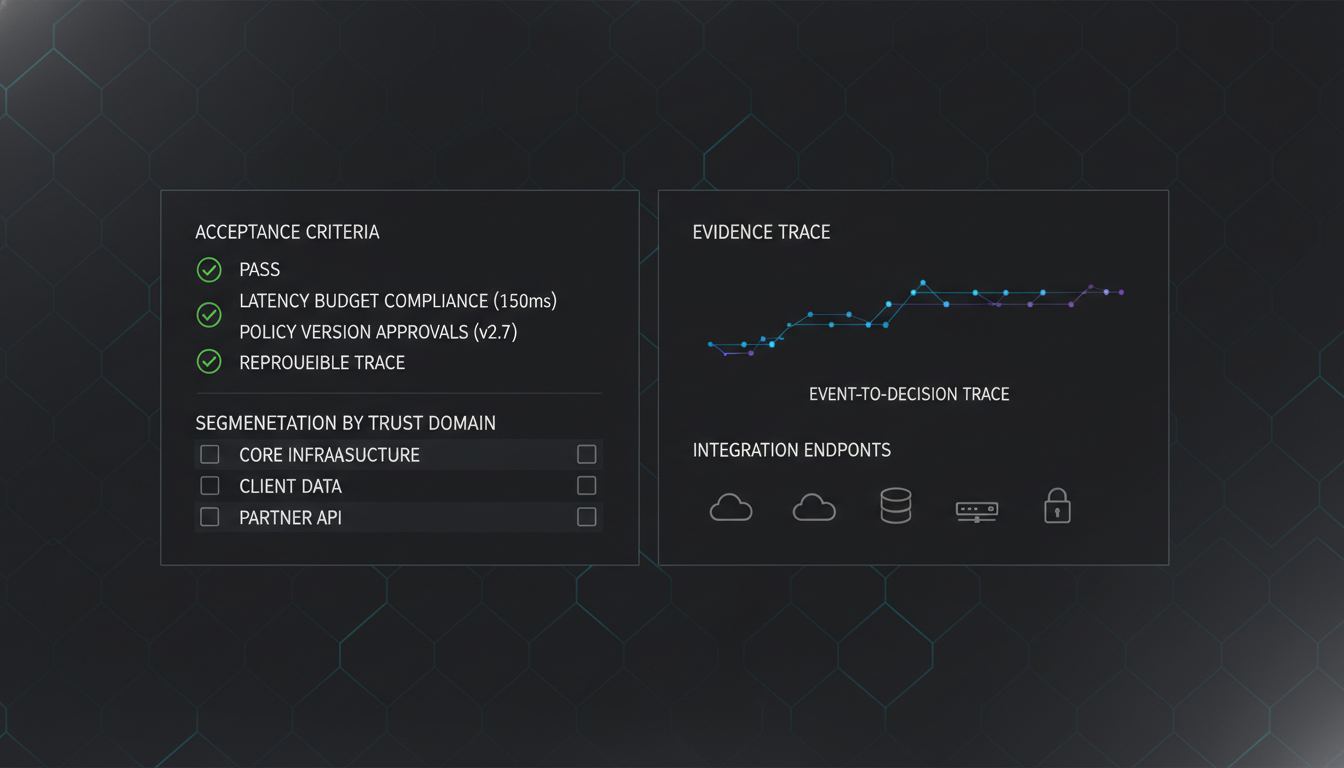
Acceptance criteria
- Latency budget meets enforcement tier requirements.
- Audit reproducibility from event to decision.
- Policy governance with versioned approvals.
- Segmentation by trust domain and role.
- Integration surfaces for data, policy, and execution.