Role in the pipeline
StørmGraph maintains event and trust graphs with typed, time-bounded edges to compute reachability sets, attack-chain candidates, and containment scope for StørmDecision.
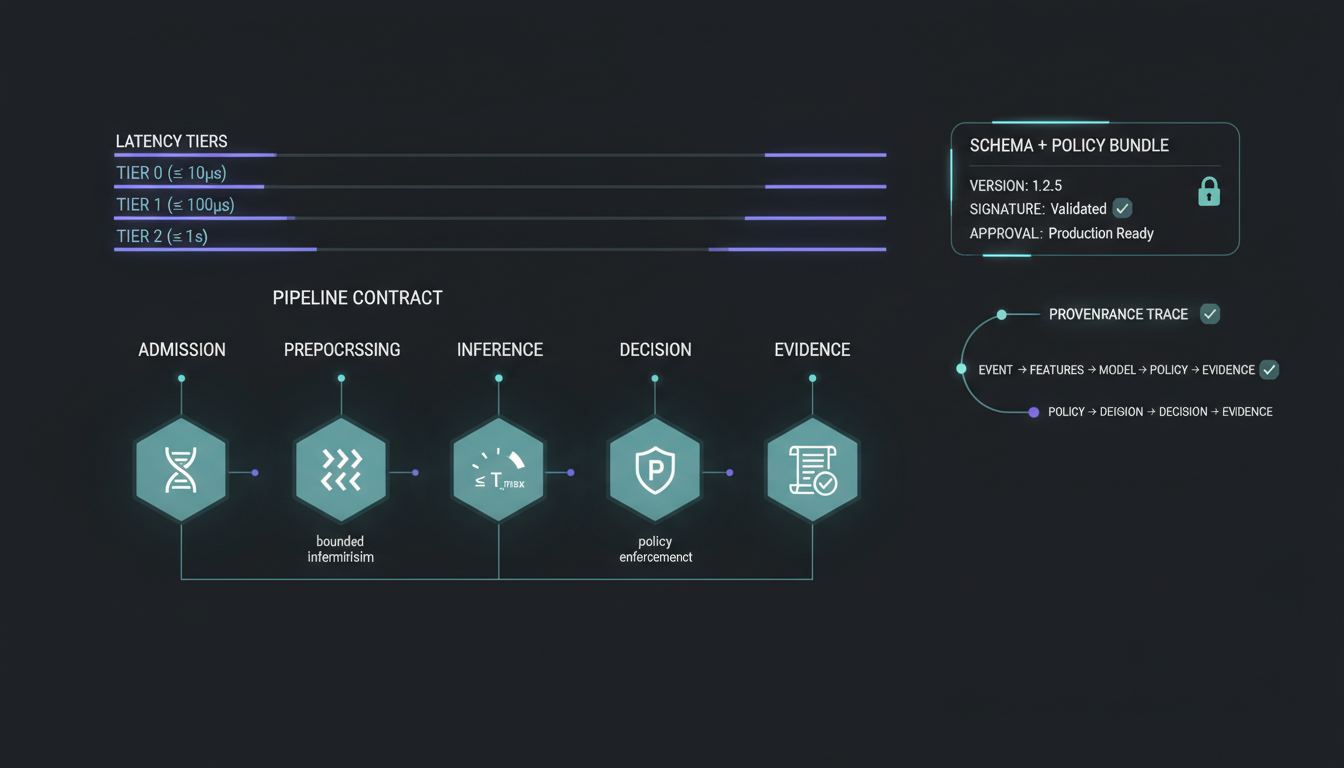
Contract: graph inputs → outputs
Typed edges and reachability outputs with sealed evidence artefacts.
Inputs
Event edges, trust edges, and policy annotations from upstream signals.
Processing
Time-bounded, typed edges with reachability and boundary queries.
Outputs
Reachability sets, blast radius, chain candidates, and sealed evidence to StørmVault.
How it works
Three steps from edges to containment constraints.
Ingest edges
Canonical entities and typed edges derived from events.
Compute reachability
Time-bounded reachability and blast-radius queries.
Emit constraints
Containment scope and signals for StørmDecision.
Interfaces
- Inputs: entities and edges from canonical events.
- Outputs: reachability sets, blast radius, containment candidates.
- Contracts: graph schema and versioning for edge types.
- Failure semantics: stale graph handling with bounded degradation.
Reachability math over event truth.
StørmGraph is a reachability engine, not a visualization layer.
It converts event streams into typed edges with time bounds.
Decisions consume reachable sets and containment scope, not raw graphs.

Bounded graph contracts.
- Edges are typed, signed, and time-bounded to preserve causality.
- Reachability sets are deterministic for the same inputs and ruleset.
- Probabilistic inputs only annotate nodes/edges; rules remain deterministic.
- Outputs include reachability, chain candidates, and containment scope.
- Graph deltas and decision context are sealed in StørmVault.
Operator controls
- Edge TTLs and expiry windows per domain.
- Trust-domain segmentation boundaries.
- Query budgets and rate limits for reachability scans.

Capabilities
Contracted graph reasoning with deterministic rulesets.
Typed, time-bounded edges
Edges encode authenticated-as, connected-to, issued-command-to, and other typed interactions with explicit time bounds. So what: graph reasoning stays causally bounded.
Compute blast radius in real time
Reachable sets and boundary crossings are computed for containment scope and decision context. So what: containment is scoped to what is actually reachable.
Path candidates from upstream signals
StørmBehaviour sequences and StørmAI inference scores annotate nodes and edges for chain candidate assembly. So what: decisions receive structured path candidates.
Actionable graph outputs
StørmDecision consumes reachability, chain candidates, and containment scope for policy-bounded actions. So what: actions are bounded to the computed blast radius.