Role in the pipeline
StørmTrust binds events to PQC-secured sessions, enforces ordering and anti-replay constraints, verifies governed artifacts before activation, and seals evidence into StørmVault. Primitive choice is deployment-specific (for example, ML-KEM/ML-DSA).

Contract: sessions + artifacts
Session binding, artifact signing, and evidence sealing.
Inputs
Sessions, governed artifacts, and trust policies for verification.
Processing
Session binding, anti-replay ordering, and signature verification.
Outputs
Verified sessions, signed artifacts, and sealed evidence records to StørmVault.
How it works
Three steps for trust continuity.
Establish PQC/hybrid session
Session establishment with deployment-specific primitives.
Bind event to session
Attach identity and session context to each admitted event.
Enforce continuity
Anti-replay ordering with rotation and revocation.
Interfaces
- Inputs: telemetry and session handshake artefacts.
- Outputs: admission controls, anti-replay ordering, and trust metadata.
- Contracts: crypto-agility policy, key rotation, and epoch bounds.
Cryptographic continuity for the pipeline.
StørmTrust is the admission and integrity substrate for all components.
It binds identity and sessions, and signs runtime artifacts.
Evidence sealing keeps decisions durable over long horizons.
Trust fabric contracts.
- PQC session binding with deterministic anti-replay ordering.
- Signed model, policy, schema, and ruleset artifacts.
- Key schedule derivation for data-plane encryption.
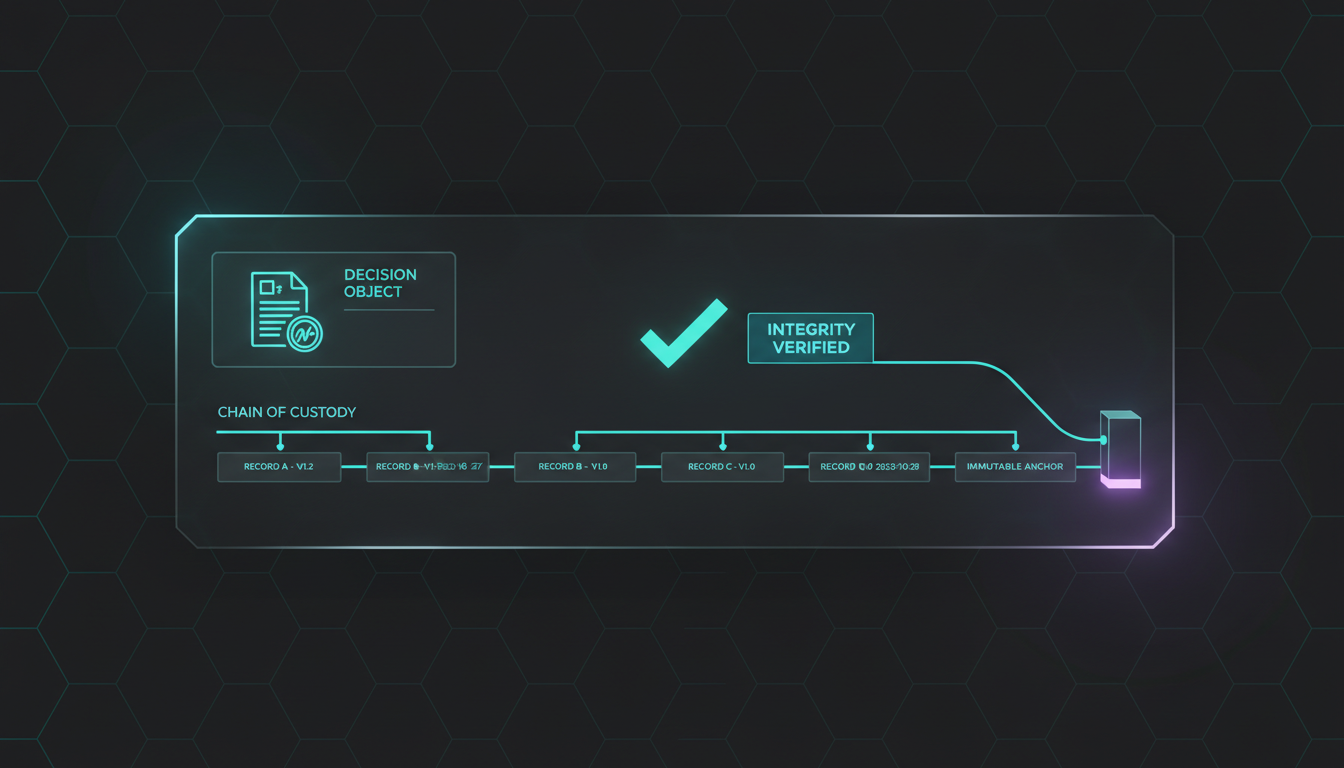
- Evidence sealing with optional immutable anchoring.
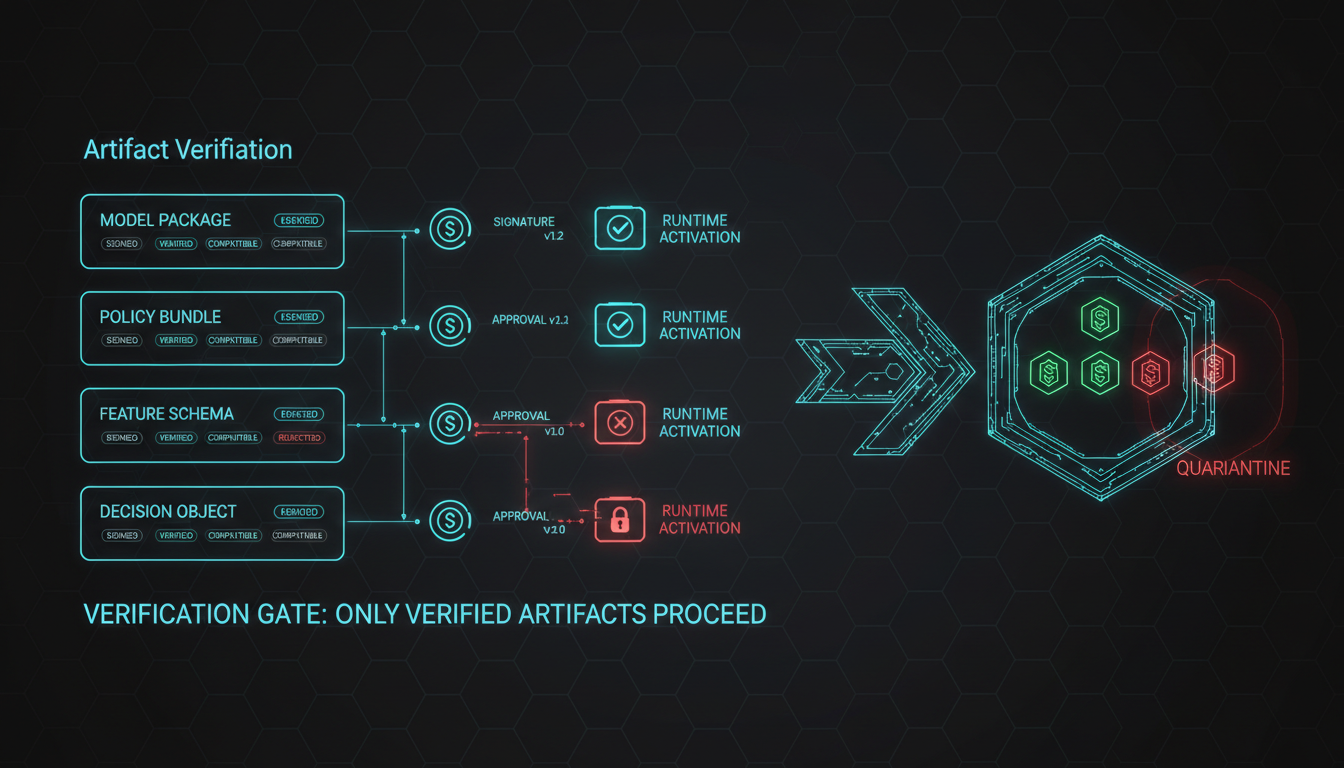
- Artefacts failing verification are rejected.
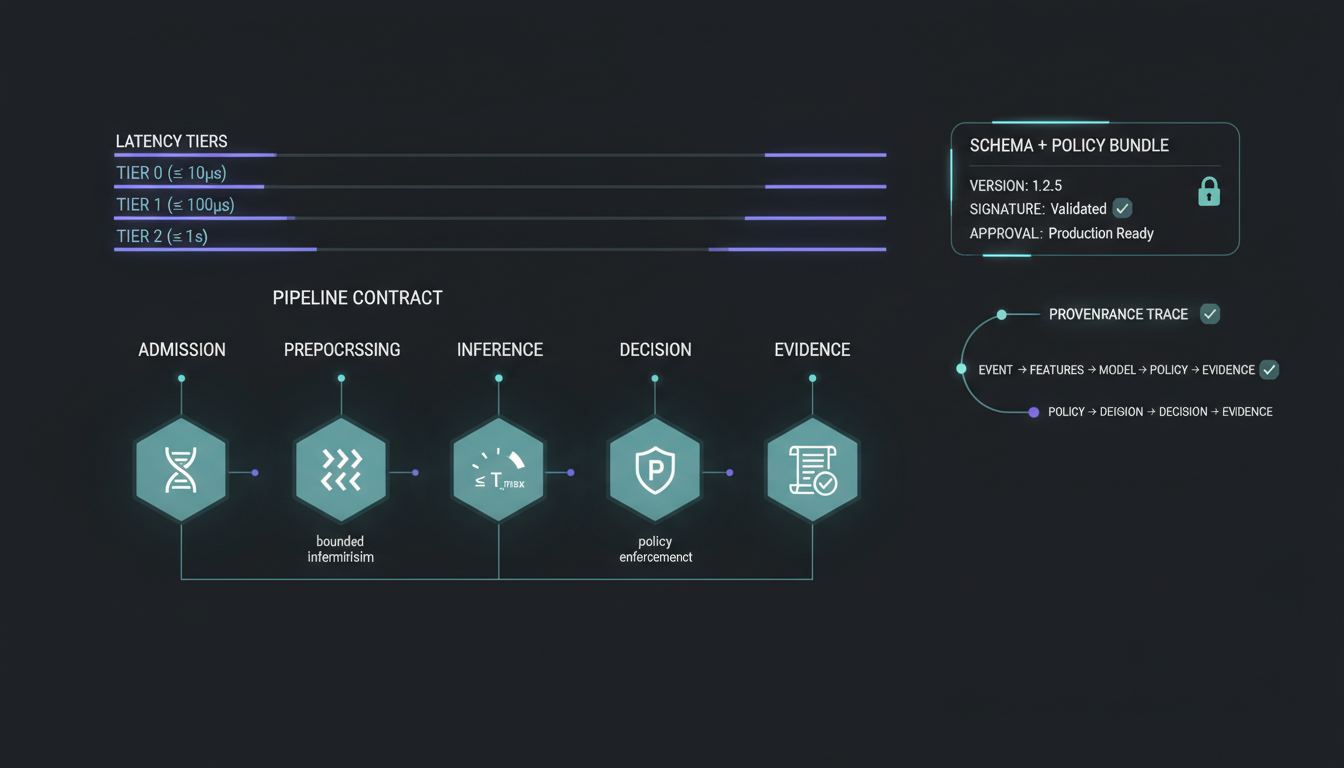
Failure modes & controls
- Anti-replay ordering blocks duplicate event admission.
- Rotation and revocation invalidate compromised sessions.
- Artifact verification failures trigger deny-by-default.
- Evidence seals prevent mutable decision records.

Capabilities
Session binding, artifact integrity, evidence sealing, and key schedules.
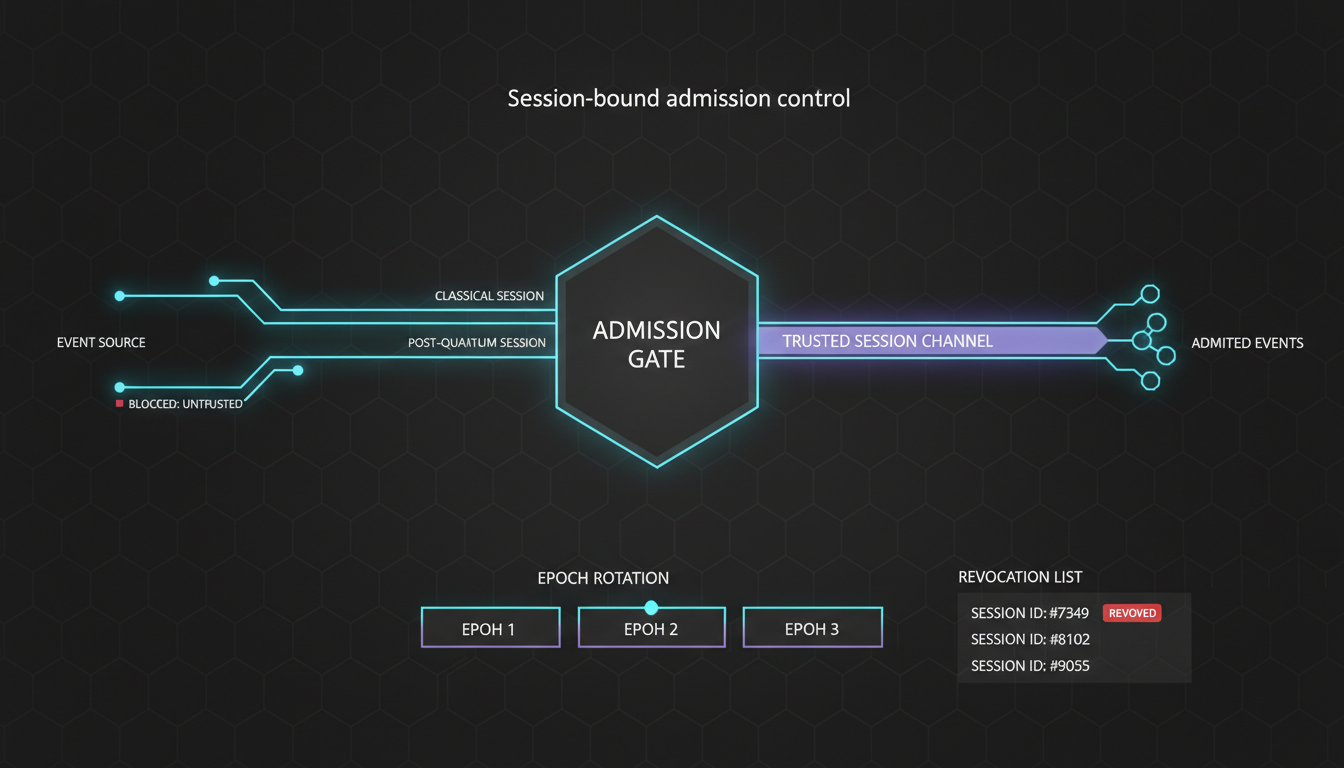
Session-bound admission control
Binds events to PQC-secured sessions with epoch rotation, revocation, and deterministic anti-replay ordering. So what: untrusted events never enter the pipeline.

Key schedule for data-plane encryption
Derives symmetric AEAD keys from PQC-established secrets for bulk payload protection. Primitive selection and schedules are deployment-specific but align with NIST PQC profiles. So what: encryption stays high-throughput and auditable.
Signed governance artifacts
Verifies model packages, policy bundles, feature schemas, graph rulesets, and decision objects before use; rejects unsigned or incompatible artifacts. So what: runtime changes are governed and traceable.
Durable evidence chain
Seals decisions and state transitions into StørmVault with tamper-evident integrity and optional immutable anchoring. So what: the audit chain remains durable.