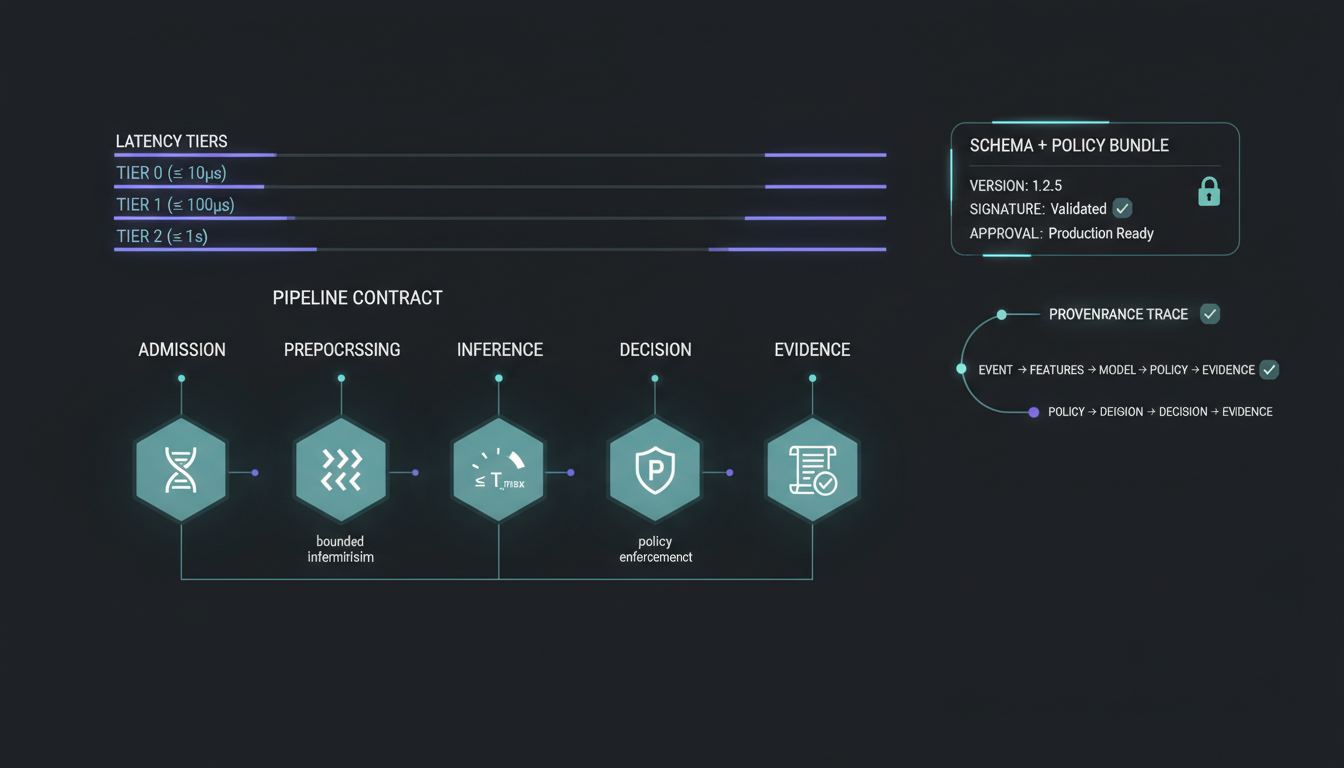
Legacy monitoring flags anomalies late; this solution ties Integrity to trusted events and bounded decisions. Event-native processing with bounded latency means integrity signals arrive inside the control window, while provable assurance means every decision is traceable to signed inputs and sealed evidence.
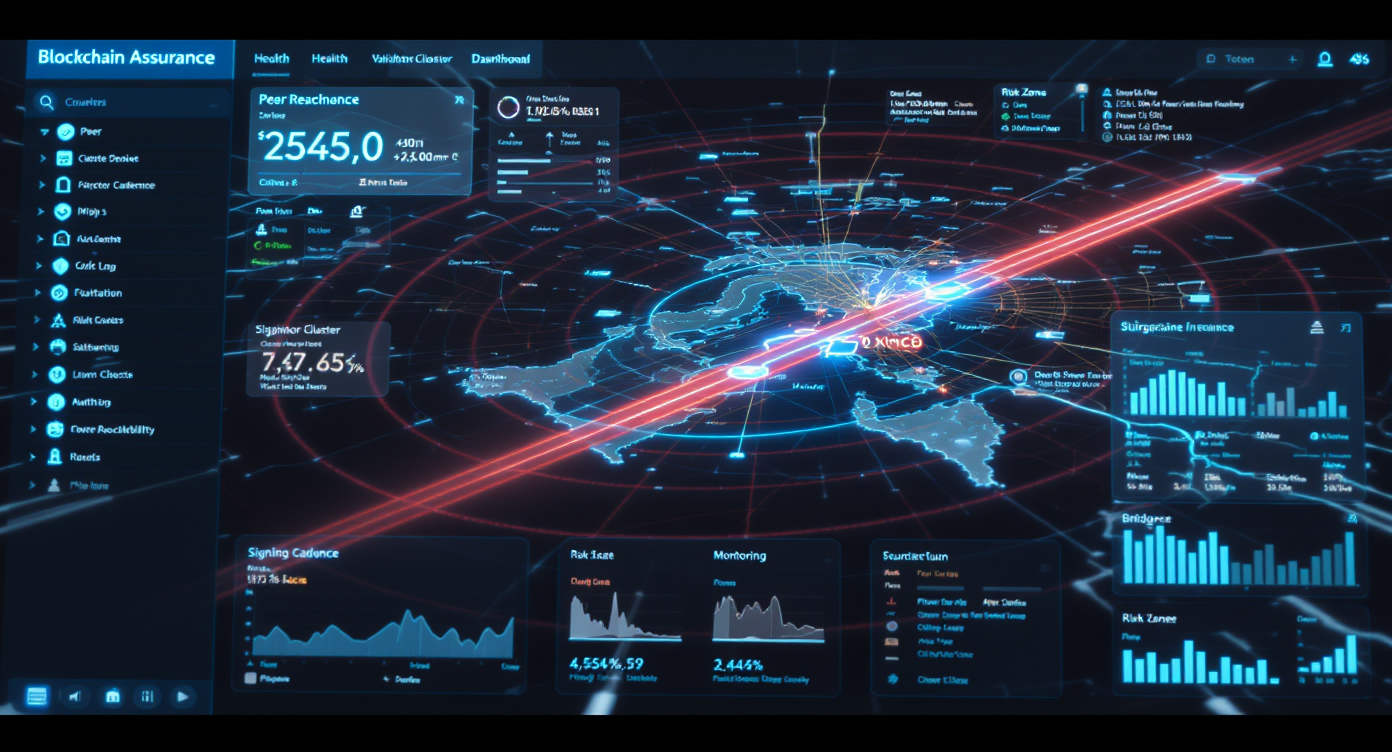
Monitor validator participation, signing operations, and bridge/oracle control paths with event-level AI.
Integrity must be enforced at the edge.
Signing paths drift before dashboards confirm risk.
Validator cadence, signing intent, and cross-chain reachability.
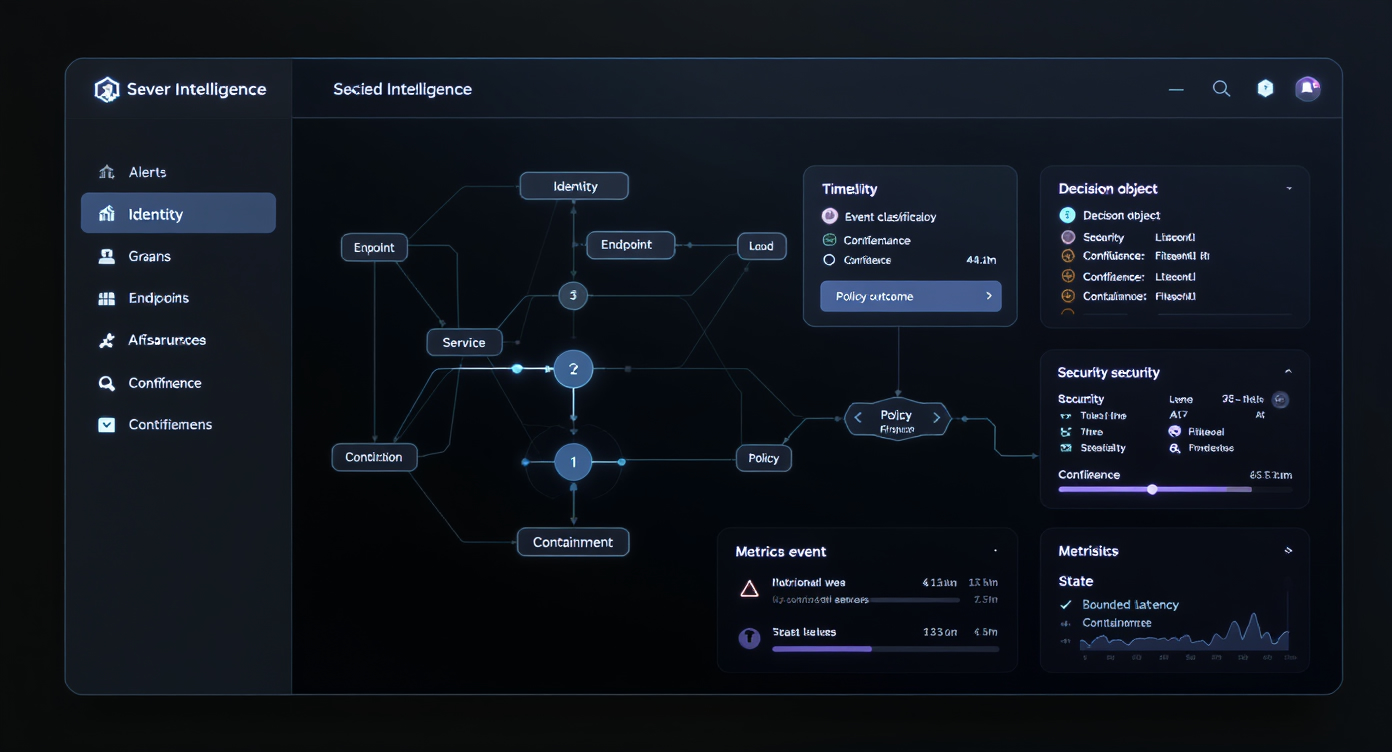
A bounded integrity decision with scope and rationale.
Faster containment with audit-ready evidence.
Integrity depends on verifiable control paths. Event-level monitoring for validators, signing services, and custody flows.
Capabilities reinforce Integrity outcomes.
Platform capabilities that enforce trust at event level across domains.
Event-level enforcement core with deterministic inference and graph reasoning.
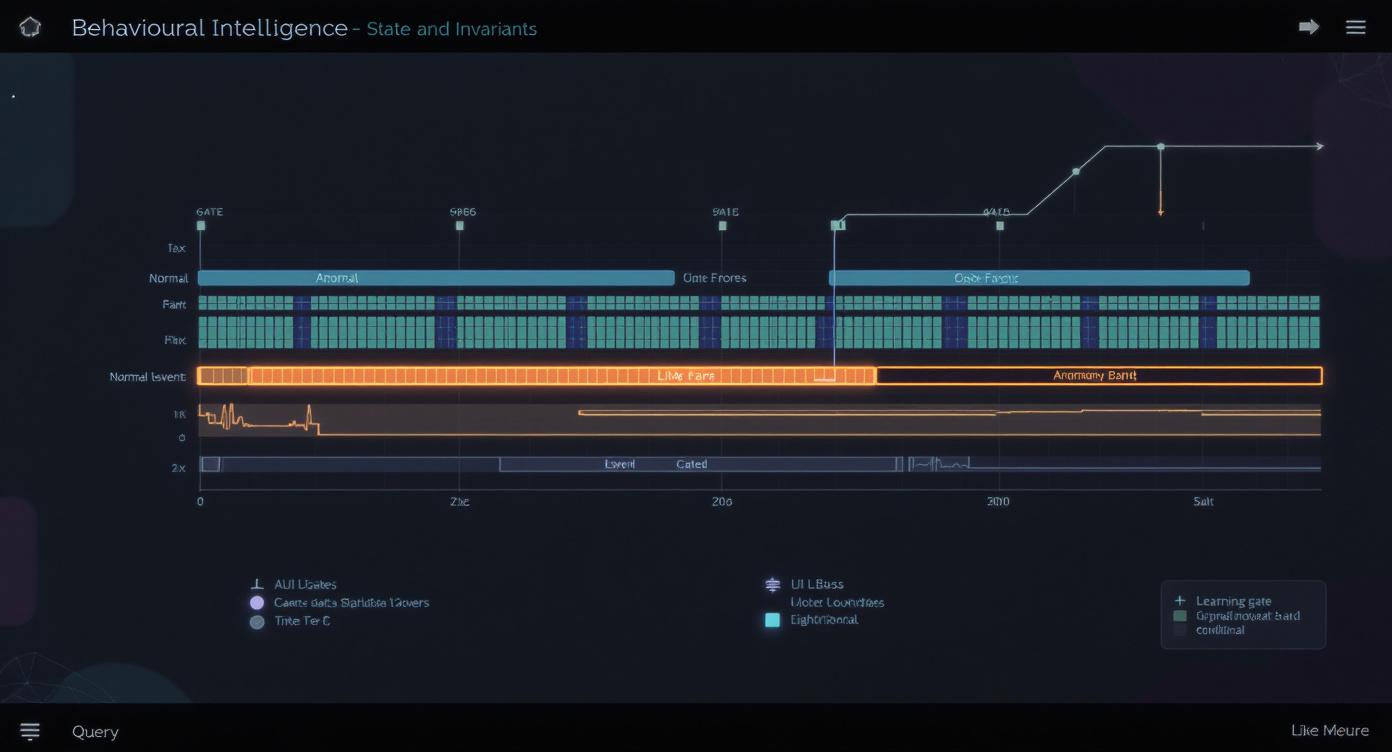
Behavioural analysis that models sequences, rhythms, and invariants.
Post-quantum trust fabric for sessions, artefact integrity, and sealed audit.
Policy-first decisioning, orchestration, and mission governance.
Integrity must be measurable under pressure.
Reduce risk across validators, signing services, and custody operations.
Detect abnormal consensus and signing cadence.
Quorum enforcement and immediate revocation.
Blast-radius controls for cross-chain operations.
Integrity depends on provable approval paths.
Protect digital asset operations with event-level enforcement.